Apr 10, 2023Ravie Lakshmanan
Threat actors are flooding the npm open source package
repository with bogus packages that briefly even resulted in a
denial-of-service (DoS) attack.
“The threat actors create malicious websites and publish empty
packages with links to those malicious websites, taking advantage
of open-source ecosystems’ good reputation on search engines,”
Checkmarx’s Jossef Harush Kadouri said[1]
in a report published last week.
“The attacks caused a denial-of-service (DoS) that made NPM
unstable with sporadic ‘Service Unavailable’ errors.”
While similar campaigns[2]
were recently observed propagating phishing links, the latest wave
pushed the number of package versions to 1.42 million, a dramatic
uptick from the approximate 800,000 packages released on npm.
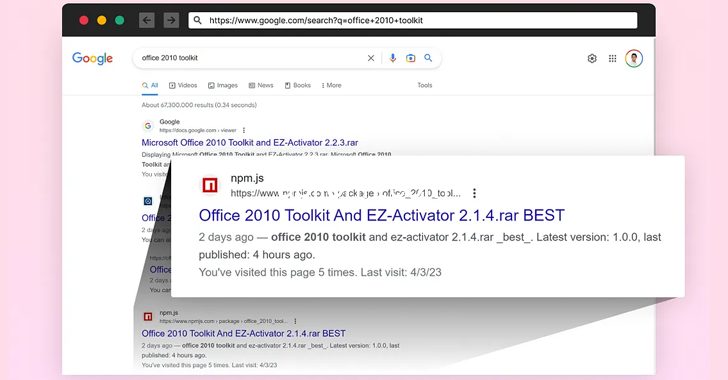
The attack technique leverages the fact that open source
repositories are ranked higher on search engine results to create
rogue websites and upload empty npm modules with links to those
sites in the README.md files.
“Since the open source ecosystems are highly reputed on search
engines, any new open-source packages and their descriptions
inherit this good reputation and become well-indexed on search
engines, making them more visible to unsuspecting users,” Harush
Kadouri explained.
Given that the whole process is automated, the load created by
publishing numerous packages led to NPM intermittently experiencing
stability issues towards the end of March 2023.
Checkmarx points out that where there may be multiple actors
behind the activity, the end goal is to infect the victim’s system
with malware such as RedLine Stealer, Glupteba[3], SmokeLoader[4], and cryptocurrency
miners.
UPCOMING WEBINAR
Learn to Secure the Identity Perimeter – Proven Strategies
Improve your business security with our upcoming expert-led
cybersecurity webinar: Explore Identity Perimeter strategies!
Don’t Miss Out – Save Your Seat![5]
Other links take users through a series of intermediate pages
that ultimately lead to legitimate e-commerce sites like AliExpress with referral IDs[6], earning them a profit
when the victim makes a purchase on the platform. A third category
entails inviting Russian users to join a Telegram channel that
specializes in cryptocurrency.
“The battle against threat actors poisoning our software supply
chain ecosystem continues to be challenging, as attackers
constantly adapt and surprise the industry with new and unexpected
techniques,” Harush Kadouri said.
To prevent such automated campaigns, Checmarx has recommended
npm to incorporate anti-bot techniques during user account
creation.
Found this article interesting? Follow us on Twitter [7]
and LinkedIn[8]
to read more exclusive content we post.
References
- ^
said
(medium.com) - ^
similar
campaigns (thehackernews.com) - ^
Glupteba
(thehackernews.com) - ^
SmokeLoader
(thehackernews.com) - ^
Don’t
Miss Out – Save Your Seat! (thehacker.news) - ^
AliExpress with referral IDs
(medium.com) - ^
Twitter
(twitter.com) - ^
LinkedIn
(www.linkedin.com)
Read more https://thehackernews.com/2023/04/hackers-flood-npm-with-bogus-packages.html