Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added[1] two vulnerabilities to its Known Exploited Vulnerabilities …



Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added[1] two vulnerabilities to its Known Exploited Vulnerabilities …

Apr 14, 2023The Hacker NewsVirtual CISO / Cybersecurity In today’s fast-paced and ever-changing digital landscape, businesses of all sizes face a myriad of cybersecurity threats. …

Apr 13, 2023Ravie LakshmananVulnerability Management Google on Thursday outlined a set of initiatives aimed at improving the vulnerability management ecosystem and establishing greater transparency measures …
Apr 13, 2023Ravie LakshmananRansomware / Cyber Attack Cybersecurity researchers have detailed the tactics of a “rising” cybercriminal gang called “Read The Manual” (RTM) Locker that …
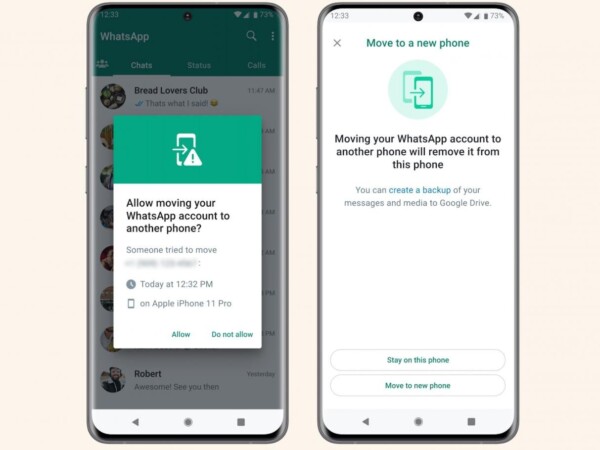
Apr 13, 2023Ravie LakshmananMobile Security / Privacy Popular instant messaging app WhatsApp on Thursday announced a new account verification feature that ensures that malware running …
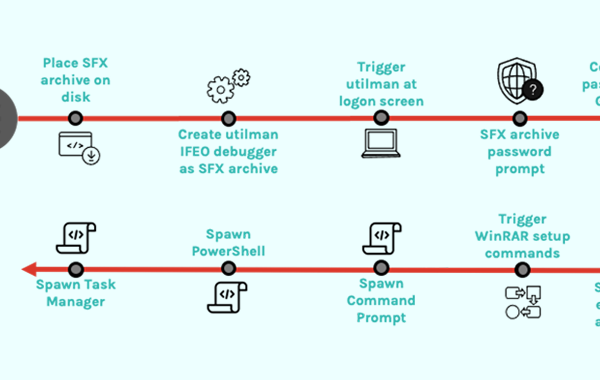
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into …

Apr 13, 2023Ravie LakshmananMalware / Cyber Attack The Transparent Tribe threat actor has been linked to a set of weaponized Microsoft Office documents in attacks …

Shadow APIs are a growing risk for organizations of all sizes as they can mask malicious behavior and induce substantial data loss. For those that …
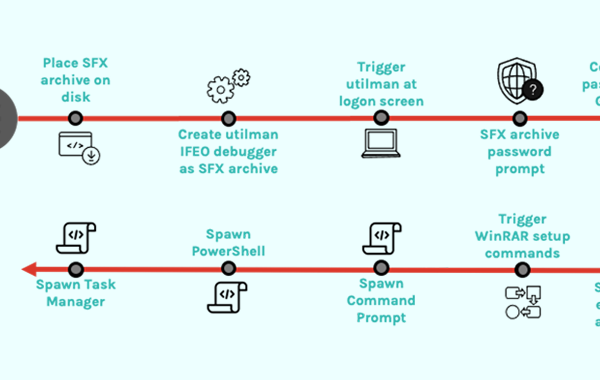
Apr 13, 2023Ravie LakshmananCyber Attack / Cyber Threat The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and …

Apr 13, 2023Ravie LakshmananSoftware Security / Bug Hunting OpenAI, the company behind the massively popular ChatGPT AI chatbot, has launched a bug bounty program[1] in …